Cyber Security Key Terms & Concepts
The CIA Triad
- Confidentiality: restrict access to only authorized subjects, e.g. encryption
- Integrity: maintain the consistency and accuracy of data over its entire life cycle, e.g. hash value
- Availability: keep the operations up and runing. e.g. maintenance and upgrade of hardware and software
Key Terms
- Vulnerability: a flaw or a loophole that can be exploited to threaten security
- Threat: an event able to cause negative impact
- Exploit: a defined way to breach the security of an IT system through a vulnerability
- Risk: the likelihood of a vulnerability to be exploited
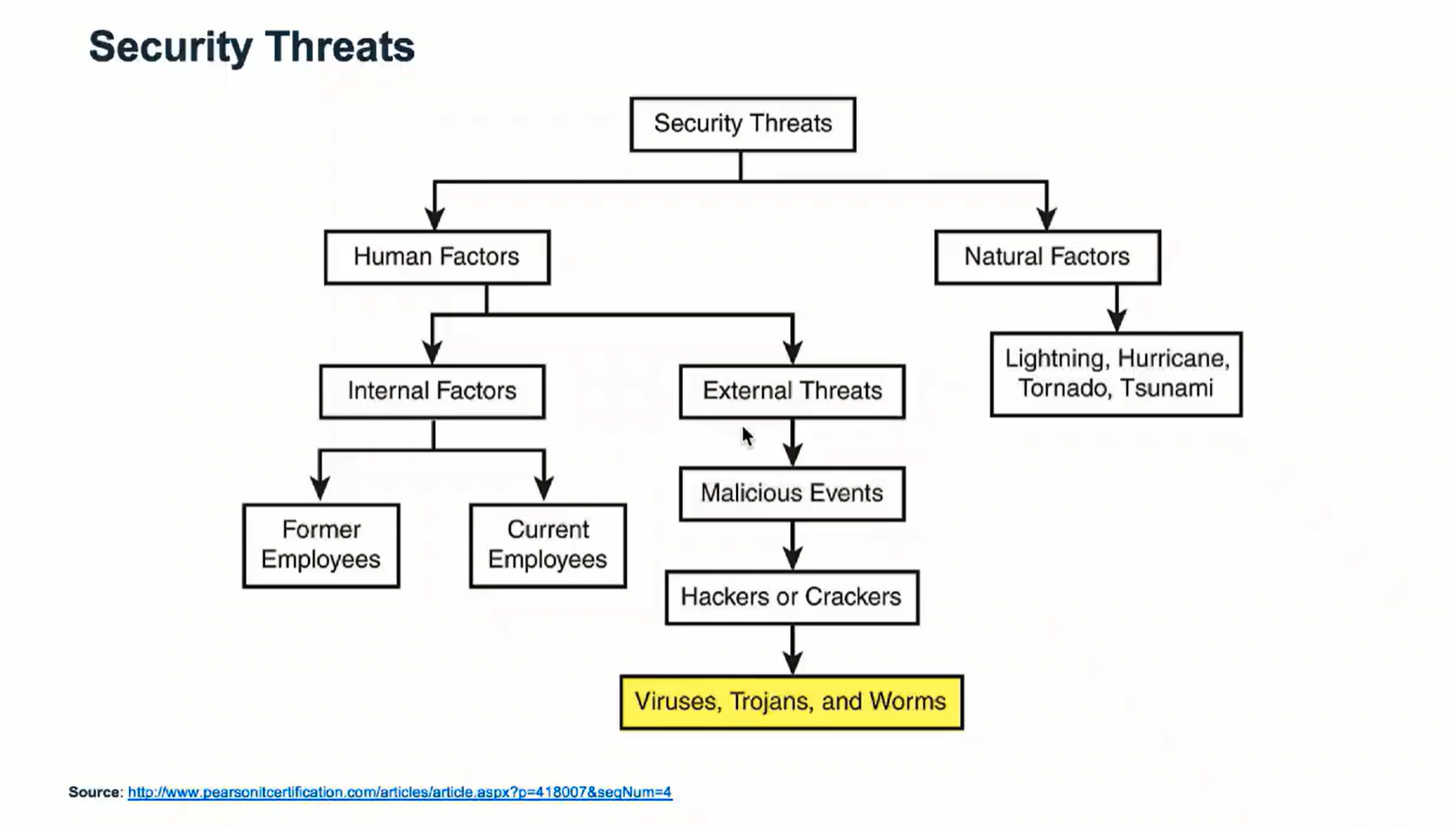
Security Threats
____
24 October 2021
Share this post: